DDoS jujitsu, or using the DDoSers mass against them
By joe
- 4 minutes read - 681 wordsWe have been under a DDoS with spambots sending us a few messages per day. Something north of 100k messages per day. I am not concerned about our infrastructure, it was holding up fine. I was more concerned about components that we didn’t have control over, or had no part in designing or building.
This begged the question: is there nothing that one can do to defend against a DDoS (email spambot) attack? It turns out that you can defend against it, if you have some control over your domain mx records. If you exercise this control, you can effect a rapid, and dramatic impact upon the botnet. Call this DDoS Jujitsu, which has been explained to me by Judoku in the past as (in highly simplified terms), the art of using your attackers attributes against them.
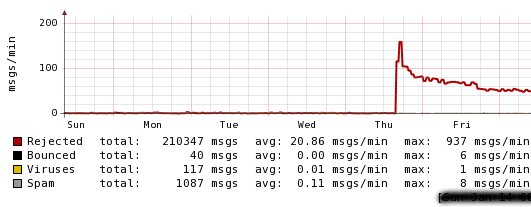
Here is the historical context. Someone on a mailing group that we subscribe to noted a large increase in recent spam. For laughs, I looked at our own internal logs. Tailing them, I noted that we were rejecting something around 1-2 spams per second. Looking over our historical log records using the excellent Mailgraph tool, I saw a large bolus of spam starting around mid thursday or so.
 Ok…. how to deal with it.
DDoS relies in part upon several internet subsystems. Including DNS.
Hmmmm….
I won’t indicate the address they were attacking. Lets call it someplace.org. Yeah, thats it. Someplace.org.
So when the little spambots wanted to bomb someplace.org, they had to do a lookup of the mail exchanger (mx record) for someplace.org. Well this pointed to our server. And hence, we were on the receiving end of lots of junk. Well, not really on the receiving end, as our antispam defensive layers are arranged so as not to allow obvious spam to move along our pipeline. As you can see, the vast majority of this was rejected out of hand. WITHOUT USING RBLS. If you are still using any form of RBL, please, please … modern technology is much better, and gives you a scalpel instead of a sledgehammer, one that adapts to new spammers instantly as compared to RBLs. One whose collateral damage is against mis-configured MTAs (Microsoft’s Exchange seems to be one of the worst offenders here, but there are lots of good reasons not to be using that for your MTA anyway).
All these spambots need to know where someplace.org is. So they look it up. And then happily try to connect to it.
Here is the Jujitsu.
We changed our mx record for someplace.org to 127.0.0.1 for about 15 minutes. Thats it. Nothing else. Then we changed it back. Did this saturday afternoon.
What? 15 minutes? This couldn’t possibly have any impact at all… right?
Have a look for yourself.
Ok…. how to deal with it.
DDoS relies in part upon several internet subsystems. Including DNS.
Hmmmm….
I won’t indicate the address they were attacking. Lets call it someplace.org. Yeah, thats it. Someplace.org.
So when the little spambots wanted to bomb someplace.org, they had to do a lookup of the mail exchanger (mx record) for someplace.org. Well this pointed to our server. And hence, we were on the receiving end of lots of junk. Well, not really on the receiving end, as our antispam defensive layers are arranged so as not to allow obvious spam to move along our pipeline. As you can see, the vast majority of this was rejected out of hand. WITHOUT USING RBLS. If you are still using any form of RBL, please, please … modern technology is much better, and gives you a scalpel instead of a sledgehammer, one that adapts to new spammers instantly as compared to RBLs. One whose collateral damage is against mis-configured MTAs (Microsoft’s Exchange seems to be one of the worst offenders here, but there are lots of good reasons not to be using that for your MTA anyway).
All these spambots need to know where someplace.org is. So they look it up. And then happily try to connect to it.
Here is the Jujitsu.
We changed our mx record for someplace.org to 127.0.0.1 for about 15 minutes. Thats it. Nothing else. Then we changed it back. Did this saturday afternoon.
What? 15 minutes? This couldn’t possibly have any impact at all… right?
Have a look for yourself.
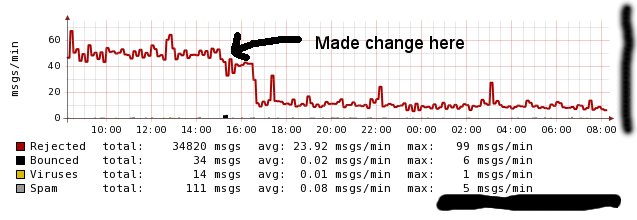 Initial impact was low, as the spambot’s had probably already acquired the address and were waiting for a random time to trigger to work their nefarious magic. Within an hour, the impact appears to be substantial.
If our theory is correct, and this is evidence of the nature of the bots, then we have just learned several important things.
Initial impact was low, as the spambot’s had probably already acquired the address and were waiting for a random time to trigger to work their nefarious magic. Within an hour, the impact appears to be substantial.
If our theory is correct, and this is evidence of the nature of the bots, then we have just learned several important things.
1. The spambot net DDoSing us is likely to be a [scale-free](http://mathworld.wolfram.com/Scale-FreeNetwork.html) network.
2. There are active defenses one might take against spambot DDoSes.
If these spambots are scale-free nets (many things are in nature) then the counter attacks can be devastating. And simple. All you have to do is break one or more of the critical assumptions of the scale free nets. Such as their ability to do a DNS search for an mx record that points to the right machine. There are other such counter-attacks, and I won’t list them. I would expect that a smart DDoS spambotnet designer will try to work around the scale-free nature of their net. This is hard as it turns out. Which means that carefully crafted Jujitsu counters may provide defense for a while. This isnt a spam solution, but a way to handle some attacks. Assuming that is, that you have the pipes and control to actively implement the defense.