Source of amusement for a monday evening
By joe
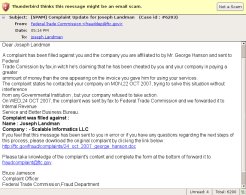
- 5 minutes read - 892 wordsUpdate 24-Dev-2007: One of the site owner listed below contacted me and asked me to remove their personal information which was contained in the site registration. I complied. I have not checked whether or not their system is still an attack host. It is very important that people with good intentions protect their systems before placing them on the net. It is generally very hard to do this for windows, and fairly easy to do this for linux. For linux, look at the Firestarter package to make setting up a firewall fairly trivial. [end of update] Alrighty. I am sitting here fighting with a now mostly functional diskless SuSE 10.2 installation, when an email arrives. In my spam box. I check that about 4 times a day. Clean it out once a month or so. Usually with 8-9000 spam. Going to have to stop looking at it … Ok, back to the story. So I get this email. It did something no other spam has done in a while. It got my attention. Here is a snapshot.
[
](http://scalability.org/images/ftc-scam.png)
Nice huh? Wakes you up for a second. Note the spelling errors. One would not expect that official US government email would come complete with spelling and grammatical errors. Ok, so the grammar may not be in error, but it is not what one might expect out of a native American english speaker. Nor would one assume that US government email would be used as a vehicle for notification of a legal issue. The US government is wedded to paper. A real issue would arrive via snail mail. Well, for maybe more than a second, I didn’t know what I was looking at. Racked my brain for all of 10 seconds trying to remember a customer by the name of George Hanson. Then I thought, well, its likely in my spam box for a reason. Lets go look at the links. No, not clicking the links, look at them. Before we do, its worth defining a useful operation from mathematics. This operation is called projection. Think of it as the shadow one vector makes on another. A vector could be pencil in this case. A value close to 1 for a set of unit length (e.g. length equals 1) vectors is probably a close match, and they point to very nearly the same thing. A value close to 0 indicates that the vectors point in different directions. So why am I telling you this? Simple. You can tell whether or not something is a phishing scam by inspection (e.g. looking at it), if you can see if the link in the href aligns with and is the same as or nearly the same as the link in the text. Both are vectors. Both point you somewhere. In this case, the critical link was indicating in text that it pointed to http://ftc.gov/fraud/complaints/24_oct_2007_george_hanson.doc, but really it pointed to modhgil.com/1maverick//media/… Hmmm… modhgil.com. Not ftc.gov. They have a projection of about 0.
landman@lightning:~/Desktop$ whois modhgil.com
Whois Server Version 2.0
Domain names in the .com and .net domains can now be registered
with many different competing registrars. Go to http://www.internic.net
for detailed information.
Domain Name: MODHGIL.COM
Registrar: ENOM, INC.
Whois Server: whois.enom.com
Referral URL: http://www.enom.com
Name Server: NS0.PROVIDER-ONE.NET
Name Server: NS1.PROVIDER-ONE.NET
Name Server: NS2.PROVIDER-ONE.NET
Name Server: NS3.PROVIDER-ONE.NET
Status: ok
Updated Date: 04-apr-2007
Creation Date: 01-apr-2005
Expiration Date: 01-apr-2009
>>> Last update of whois database: Mon, 29 Oct 2007 22:27:00 UTC < <<
...
Domain name: modhgil.com
Registrant Contact:
MODHGIL.COM
[deleted at request of site owner]
GB
Ok, I am snickering now. I ran over to the FTC’s site to see if they had any news of this, and sure enough, on the first page
For laughs, lets see if this is a compromised machine.
nmap modhgil.com
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-29 18:29 EDT
Interesting ports on p1host5-shared.provider-noc.net (87.236.89.24):
Not shown: 1684 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
25/tcp open smtp
53/tcp open domain
80/tcp open http
106/tcp open pop3pw
110/tcp open pop3
143/tcp open imap
443/tcp open https
465/tcp open smtps
993/tcp open imaps
995/tcp open pop3s
8443/tcp open https-alt
Well, it looks like someone has a few too many open ports, but it could just be part of the ruse. The email itself seems to have come from s20.80code.com. This could be forged though. Remember when whois used to give you range information for IPs? Ahhh the good old days. Now we just see this address. Well, for laughs, lets ping the s20.80code.com. Yup, the IP address maps back into is what is in the mail header. There is a real web site there. It looks like a real business. The problem is that the headers may have been forged. So we know the email is a fraud, took about 10 seconds to figure that out. What did my automated tagging pipeline say (all mails traverse this):
X-Spam-Report:
* 5.0 BOGOFILTER Bogosity: bogofilter thinks this mail is crap
* 1.5 HTML_IMAGE_ONLY_20 BODY: HTML: images with 1600-2000 bytes of words
* 0.0 HTML_MESSAGE BODY: HTML included in message
* 0.0 BAYES_50 BODY: Bayesian spam probability is 40 to 60%
* [score: 0.5000]
* 1.9 MIME_HTML_ONLY BODY: Message only has text/html MIME parts
* 1.2 MIME_HEADER_CTYPE_ONLY 'Content-Type' found without required MIME
* headers
Yup, I think Bogofilter summed it up nicely.